On Friday, 21 October 2016, many internet users could not reach marquee internet destinations like Amazon Web Services, Twitter, Spotify, Netflix, Slack, PayPal, and many others. Why not? Dyn, a large Domain Name Service (DNS) provider, was under attack.
At roughly 7:00am North American Eastern Time, Dyn began experiencing a Distributed Denial of Service (DDoS) attack. It took Dyn’s east-coast DNS down twice in one day. This DDoS was different than most, for a few reasons:
- It took the DNS provider down for a good two hours before it was able to effectively mitigate the first wave of the attack and bring its east-coast services back up.
- There were second and third wave attacks, the second starting at noon, which took an hour to mitigate and restore service. The third attack was attempted, but Dyn was able to mitigate that one without customer impact.
- This attack came from tens of millions of IP addresses, leveraging compromised Internet-of-things (IoT) devices such as security cameras and ‘smart’ household gadgets that had not been properly secured.
- Most DDoS attacks are against a single, specific target. By going after Dyn, the perpetrators successfully brought down multiple sites.
DDoS attacks are not uncommon. According to the Q2 2016 State of the Internet – Security Report published by the Content Distribution Network (CDN) provider Akamai, it witnessed 4,919 DDoS attacks. Put another way, that’s over two every hour on average.
 Dyn is still conducting its forensic investigation, and it will likely take some time to get to not just a full understanding of what happened, but how to effectively deal with it going forward. There will be a lot of lessons learned from this incident, which will hopefully make the internet stronger. However, there is one ‘after effect’ that individuals and companies should be cognisant about, and that’s the ‘echo effect’ of this episode.
Dyn is still conducting its forensic investigation, and it will likely take some time to get to not just a full understanding of what happened, but how to effectively deal with it going forward. There will be a lot of lessons learned from this incident, which will hopefully make the internet stronger. However, there is one ‘after effect’ that individuals and companies should be cognisant about, and that’s the ‘echo effect’ of this episode.
Because so many premium-brand sites were impacted by Dyn’s compromise, coverage even in mainstream news and media has been extensive. Combined with other notable hacks of late (the eMail account breach at Yahoo! compromising half a million accounts, the Ukrainian power grid DDoS, Hollywood Presbyterian Hospital and University of Calgary ransomware attacks, and the SWIFT vulnerabilities allowing the $81 million fraudulent transfer of funds from the Bangladesh Bank, just to name a few), there will be a heightened anxiety amongst internet users, and that translates into better-than-average phishing opportunities for hackers.
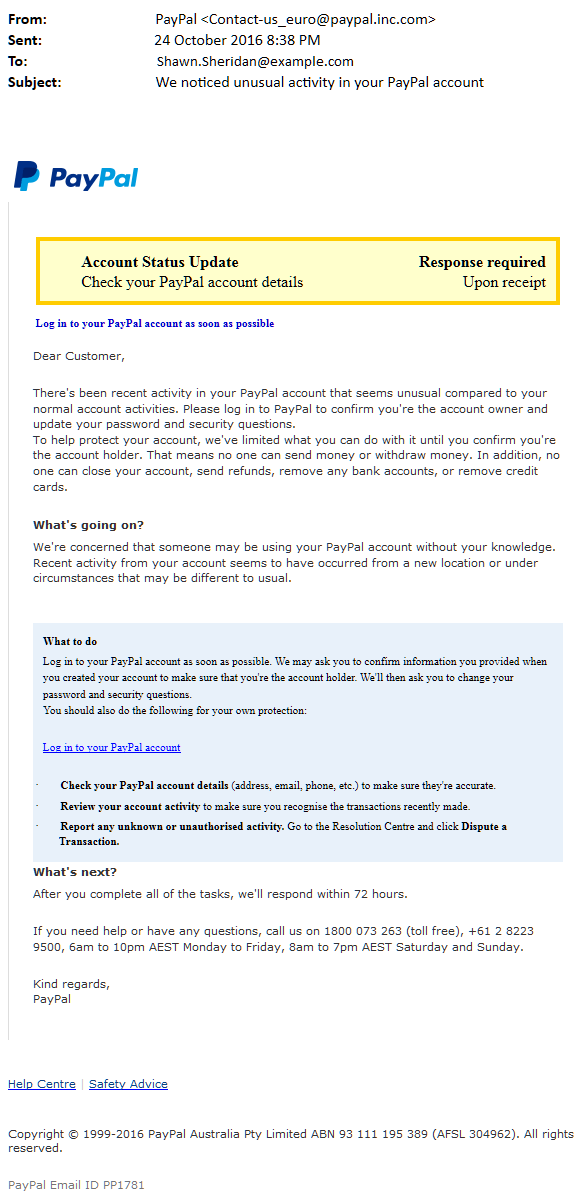
For example, I received the eMail message to the right just days after the Dyn attack. Looks pretty innocuous, right? And with the sensational attack on Dyn, and PayPal being one of their customers, it could very well be the case that my account was compromised. However, there are a few problems with this eMail:
- The sender’s domain at first glance looks legitimate, but look closer. The domain is actually “inc.com”, which is not PayPal. PayPal’s domain is PayPal.com. "paypal.inc.com" is in fact a subdomain of "inc.com". If the subdomain existed at some point, then someone with access to inc.com's DNS was able to set up so that it might be missed without careful inspection (and inc.com should be worried). But at the time of writing this article, that subdomain didn't exist, and indeed it didn't have to when the phisher sent out the eMail. eMail address spoofing is literally child's play.
- The sender’s eMail address also looks like it’s from European PayPal, yet in the messages footer and elsewhere in the eMail, it cites PayPal Australia, with Australian phone numbers, time zones, and other elements.
- If you hover over the link to supposedly log into your PayPal account, here’s what you get:
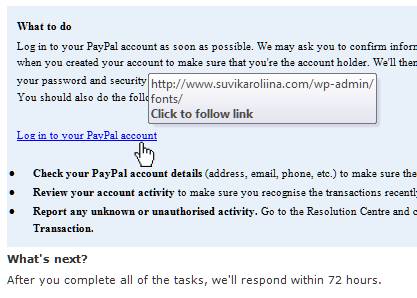
That certainly isn’t a PayPal site. But clicking it is what the phisher wants you to do. I didn’t.
Of course the last clue was that I in fact don’t have a PayPal account, in Australia or anywhere else. So, sadly for the phisher, I was going to be a fail from the get-go.
There will be many more such attacks in the coming weeks as hackers attempt to capitalise on Dyn’s misfortune. Stay vigilant, educate yourself and your staff, and don’t get caught!
See Dyn's statement here: http://dyn.com/blog/dyn-statement-on-10212016-ddos-attack/